Lab 3 - Security & Compliance Management - ROKS
Note: ‘This lab is to be used for CP4MCM 2.1.X on ROKS.’
Lab Overview
IBM Cloud Pak for Multicloud Management provides consistent visibility, automation, and governance across a range of multicloud management capabilities such as cost and asset management, infrastructure management, application management, multi-cluster management, edge management, and integration with existing tools and processes. Customers can leverage Cloud Pak for Multicloud Management to simplify their IT and application ops management, while increasing flexibility and cost savings with intelligent data analysis driven by predictive signals.
IBM Cloud Pak for Multicloud Management helps companies make the transition from traditional monitoring systems to cloud-based ones more easily. It effectively monitors all kinds of IT resources in a hybrid environment. It helps Operation teams manage hybrid environments without hiring new personnel to support each new technology that is being used by developers.
This Tutorial explores how to use governance and compliance features to manage your multicloud environments with a consistent set of configuration and security policies across all applications and clusters.You explore the following key capabilities:
Understand Cloud Pak Policy and GovernanceLearn to create and customize policies with the out of the box policy templatesLearn to use namespace policiesLearn to use network policies
Prerequisite
- You need to have your personal CP4MCM on ROKS environment (check here how to request it).
- You need to pre-install all necessaries CLI tools (check here how to install them).
- If you didn’t complete the Lab 1 - Multicluster Management, you need, at least, to complete the steps of Add Managed Clusters to have your clusters ready on CP4MCM to be able to follow this lab.
Business Context
As a member of the Security Operation (SecOps) team, you are having problems to minimize risks and identify policies violations in your multicloud hybrid world. Manage a Security Policy for all your cloud-based services and data across multiple providers is overwhelming your team. Your company is deploying multiple Kubernetes clusters to address their specific needs. Some Dev teams are deploying clusters across public and private clouds, and some are deploying clusters across regions, and some are deploying clusters to support the development and test needs.
As different teams deploy more clusters, new challenges are introduced:
- How do I set consistent security policies across environments?
- Which clusters are compliant?
Because of that, you want to explore how IBM Cloud Pak for Multicloud Management, provides consistent visibility, governance and automation of your complex environment.
IBM Cloud Pak for Multicloud Management Governance and risk dashboard allows you to view and manage the number of security risks and policy violations in your clusters and applications. Policy templates are used to create one or more policies for third party or external security controls. For example, you can create a mutation policy with the mutation policy controller. Each policy document can have at least one or multiple templates.
By using policy-based role and compliance management, you are able to:
- Set and enforce polices for security, applications, and infrastructure or auto enforcement at the cluster level.
- Check compliance against deployment parameters, configuration, and policies.
- Automatically remediate violations.
In this tutorial, you create and enforce the following governance policies:
Namespace policyNetwork policy
Namespace Policy
Kubernetes namespaces help organize cluster resources between multiple users and split the resource quote. Cluster administrator might restrict the user to use specific namespaces for applications. The namespace policy allows you to catch cluster violations when namespaces are not defined as per the policies.
A sample namespace policy resemble the following:
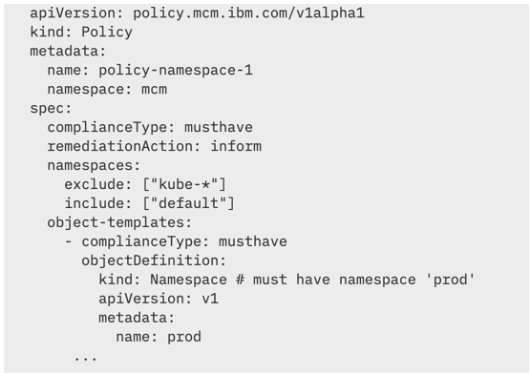
In this section, you create a policy that ensures that a specified namespace is present in clusters that match the selection criteria.
1.Open the Terminal window.
2.Let’s use the ROKS Managed Cluster context:
kubectl config use-context roks-managed-cluster
3.Later you will create a Policy to inform/enforce a namespace in your cluster. Let’s verify that you don’t have this namespace by now. Run the command below:
oc get ns | grep k8demo
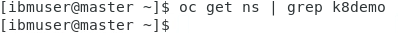
So far, you don’t have the k8demo namespace. Great! Let’s create a Policy to inform when your cluster is not compliance with a namespace policy.
4.Back to the IBM Cloud Pak for Multicloud Management Web Console page on your browser (If you don’t have the CP4MCM Console opened, check here how to access it).
On the top-left of the page, open the Menu (1) and select Govern risk (2).
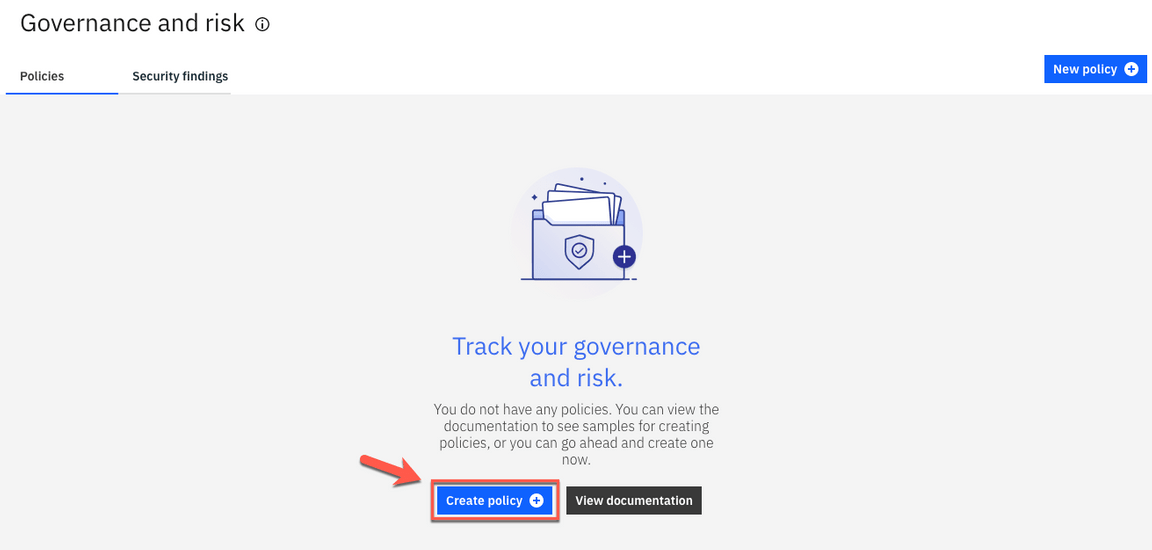
5.Here you see the Policy tab. This view displays the policies that have been created and the dashboard of policy compliance for each cluster. By now, you don’t have any Policy created. Let’s do it! Click Create policy.
6.On the Name field type policy-namespace (1), on the Namespace field select default (2), on the Specifications field select namespace (3) and on Cluster binding select environment: QA (4).
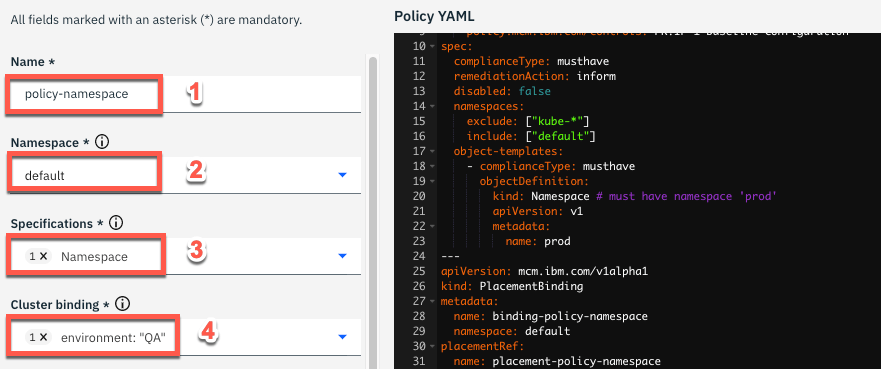
7.Now, let’s change the namespace name value. In the YAML file section, on the right, change the name attribute from prod to k8demo. With that, you are creating a Policy to verify if you have a k8demo namespace/project in your cluster.
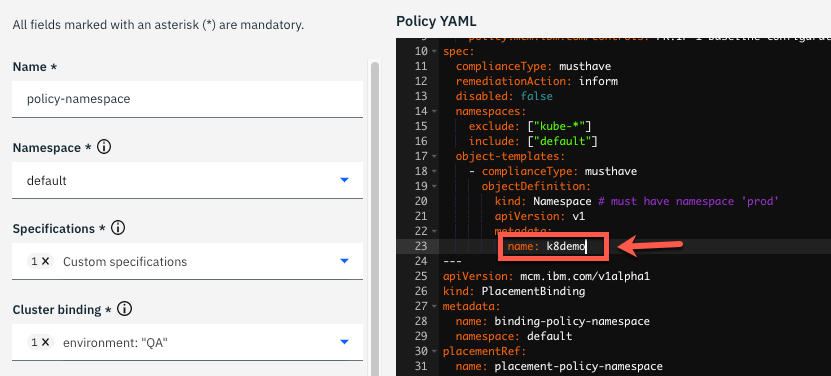
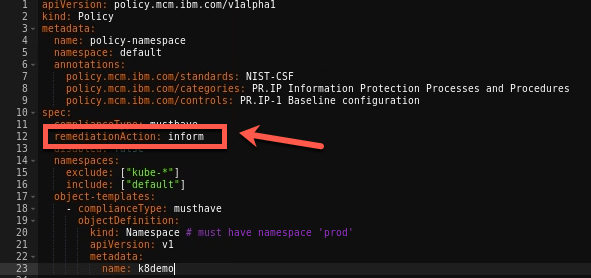
8.Notice that the policy is set to inform rather than enforce. With value inform, the policy only reports whether the cluster is compliant to the specified policies. With value enforce, the policy provides automatic remediation. Keep inform value by now.
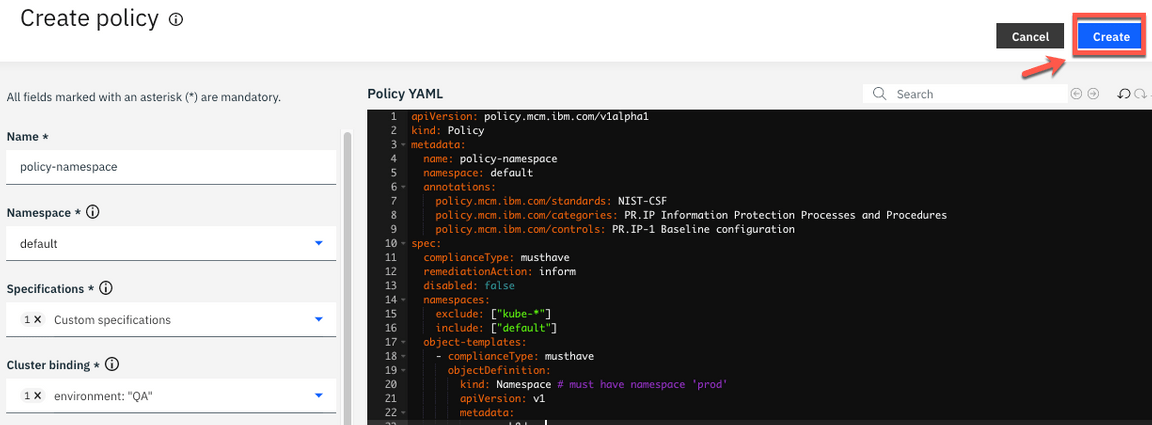
9.Click the button Create to create your new policy.
10.In a few seconds, the policy controller will check if the namespace k8demo is present and provides information regarding the current compliance of the policies. Remember, you did not enforce this policy. Instead we specified inform. As such, the Governance and risk view displays a policy violation in our cluster, as illustrated below.
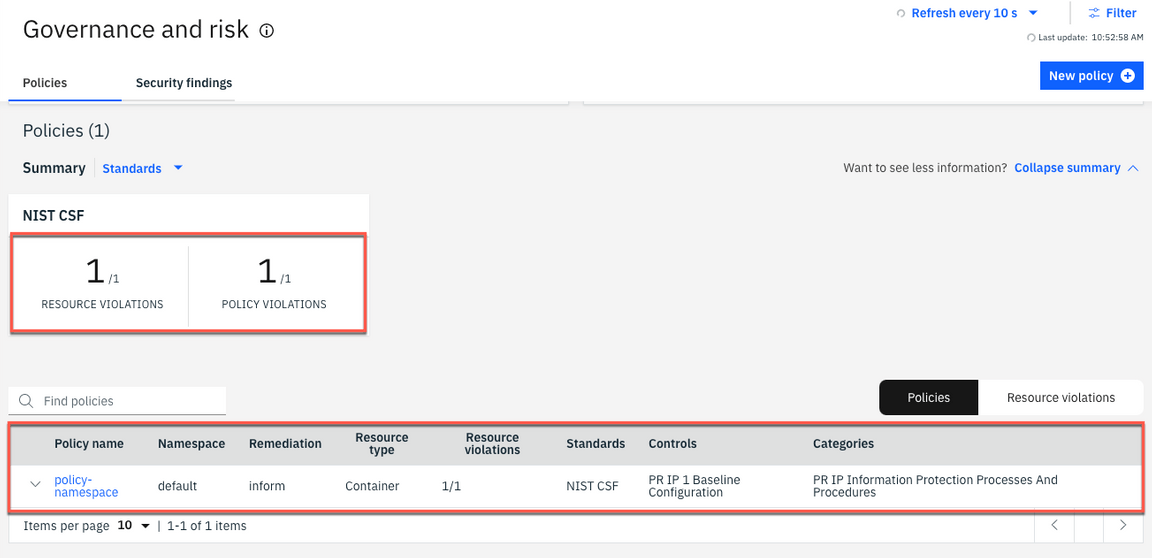
11.Click the Resource violations link to find which cluster is violating the policy.
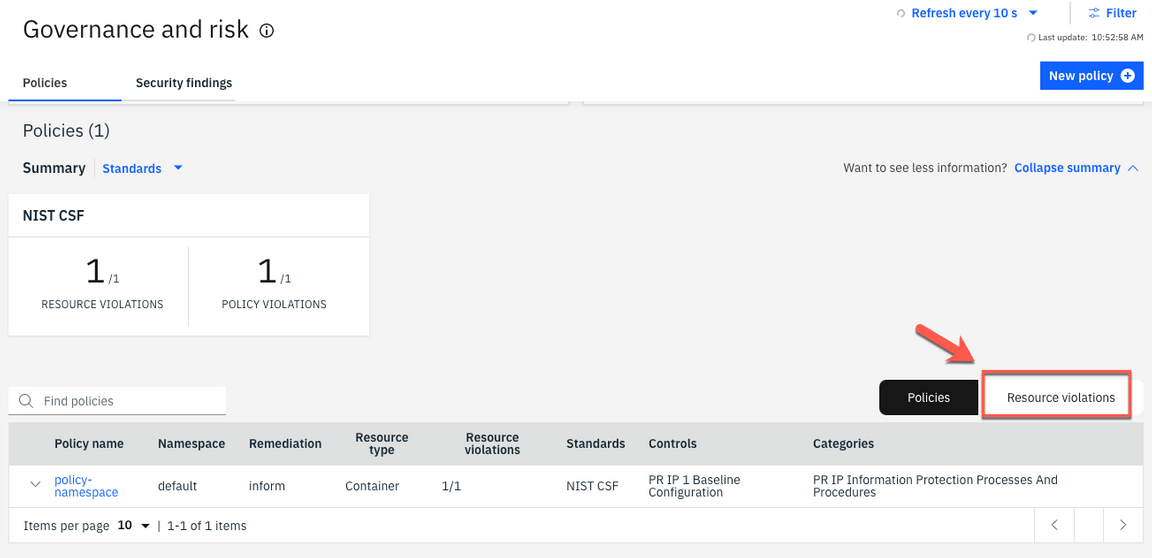
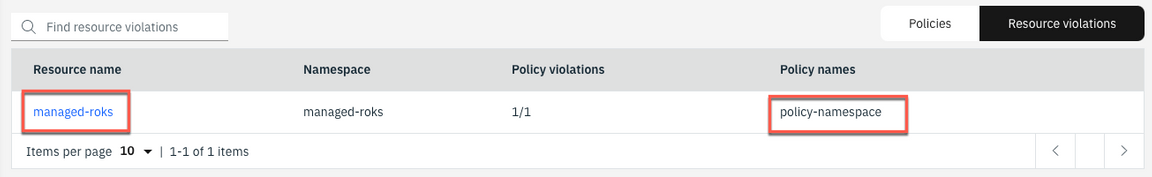
12.The managed-roks cluster is in violation of the policy which requires a namespace that is called “k8sdemo” to exist.
13.The managed-roks is the same cluster that you verified in the first step of this section that k8sdemo namespace does not exist. Hence it shows that there is no namespace k8demo in the cluster.
14.Now, let’s verify the k8demo namespace still does not exist. Back to the terminal window, run the command below:
oc get ns
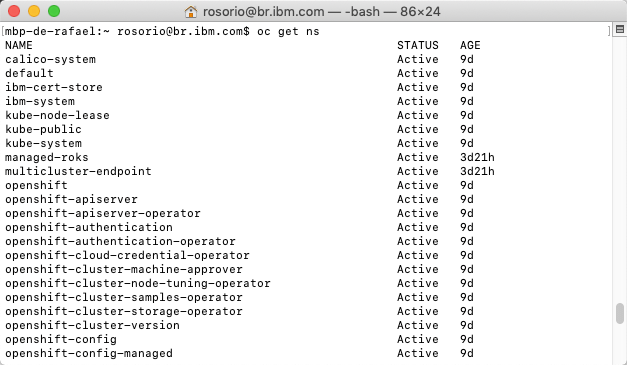
There should not be a namespace named k8demo listed, which indicates that the policy did not enforce it to be created.
15.Back to the browser. Now, let’s change the policy to be enforced. In the policies view, click on POLICY VIOLATIONS.
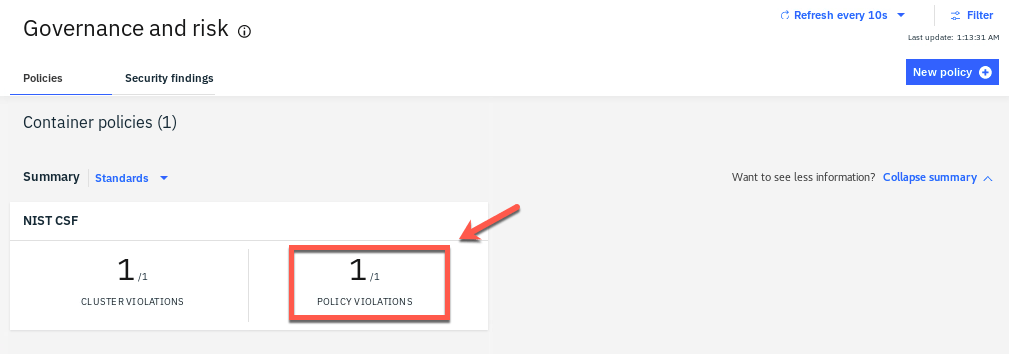
16.Click the policy-namespace link.
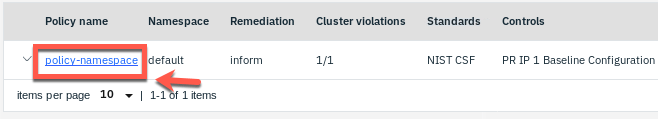
17.Open the YAML tab.
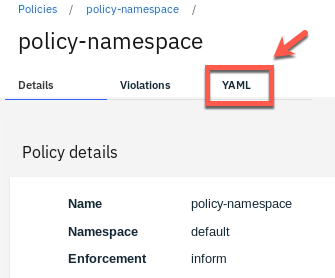
18.Click the Edit button to go into edit mode to modify the YAML file.
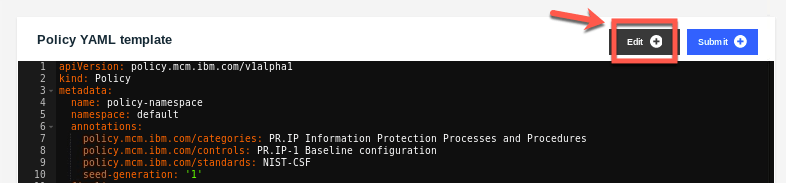
19.Change the value of remediationAction: inform to remediationAction: enforce.
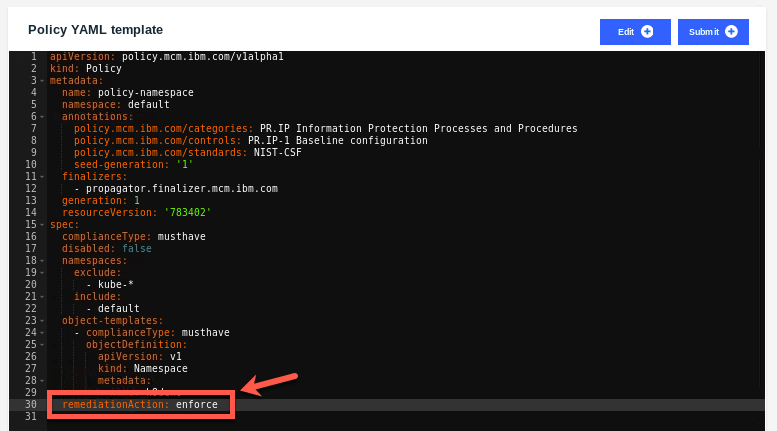
20.Click the Submit button to save the change.
21.Open the Details tab.
22.A few seconds later, the policy violation is automatically removed.
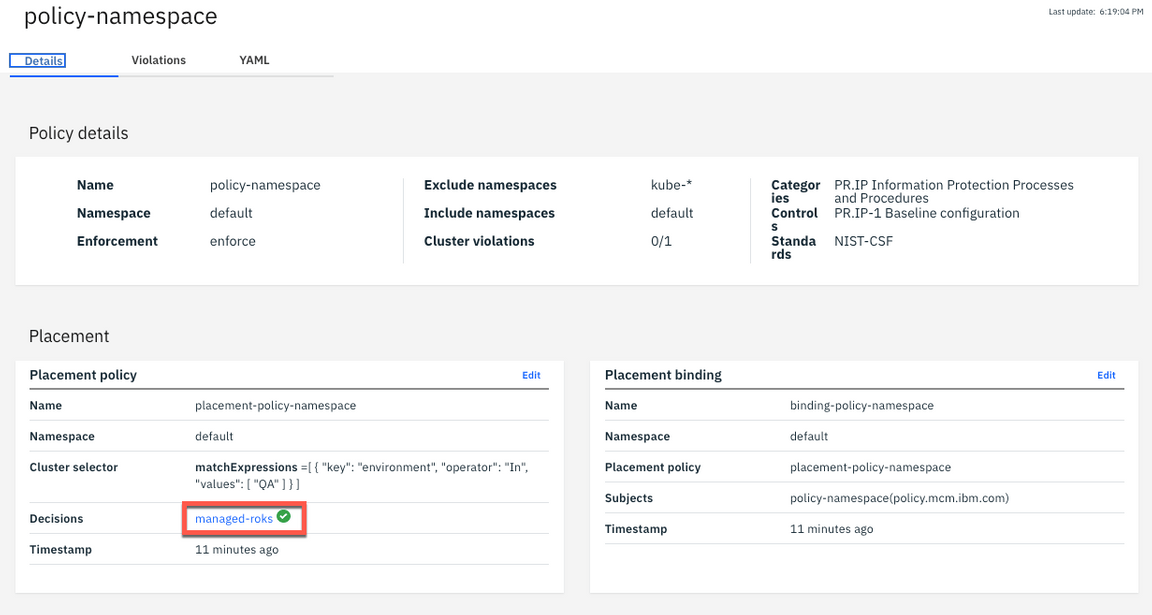
23.Open the Violations tab.
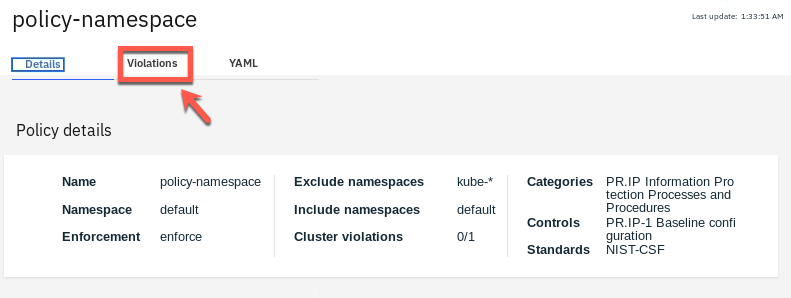
24.You also can validate the same from the Violations view: No Violations are available.
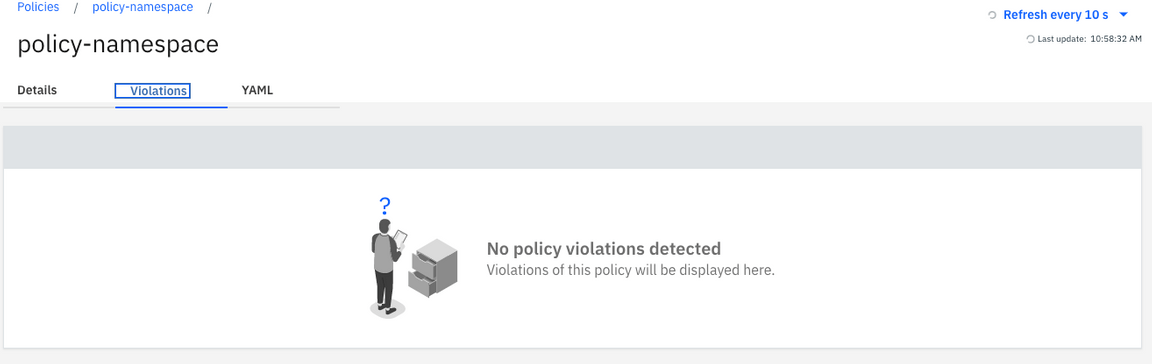
25.Now, let’s check how the policy on enforce mode, removed the violation. Back to the terminal window, run the command below, to ensure that the k8demo namespace is created in the cluster.
oc get project | grep k8demo

You have successfully implemented the Namespace Policy!
Network Policy
A network policy is a specification of how groups of pods are allowed to communicate with each other and other network endpoints.NetworkPolicy resources use labels to select pods and define rules which specify what traffic is allowed to the selected pods.
Apply the network policy to define which network request to deny. For more information about network policies, refer to this documentation.
A sample network policy resembles the following:
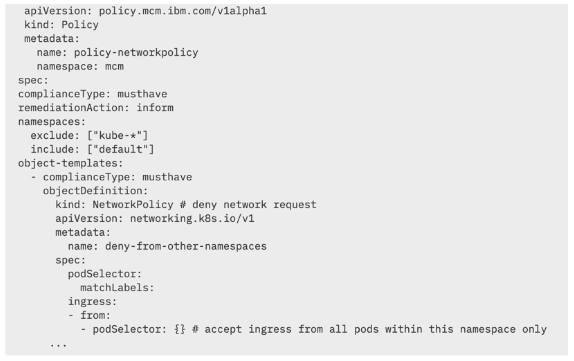
IBM Cloud Pak for Multicloud Management enables your team to check and enforce network policy compliance against your multiple clusters in your hybrid environment.
In this section, you learn how to create a Network Policy in IBM Cloud Pak for Multicloud Management. This lab needs an application that has at least two pods with services where one pod needs to connect to other pod’s associated service. You will use the application Quote of the Day that is already deployed on the cluster in the default project.
1.Back to the CP4MCM Console page tab on your browser, click Policies link on navigation breadcrumb.
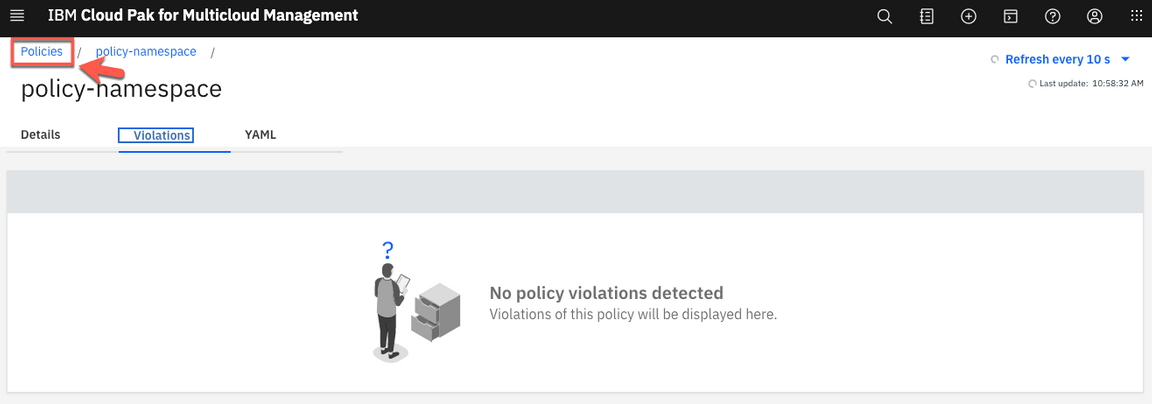
2.On the Policies view, click New policy.
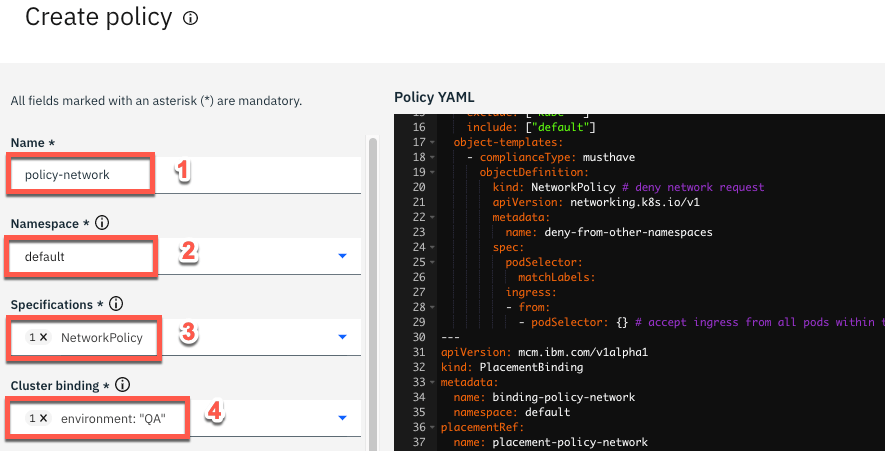
3.Enter policy-network as name of the policy (1), select default as namespace (2), on specifications field choose NetworkPolicy – deny network request (3). On the cluster binding field select environment: QA (4).
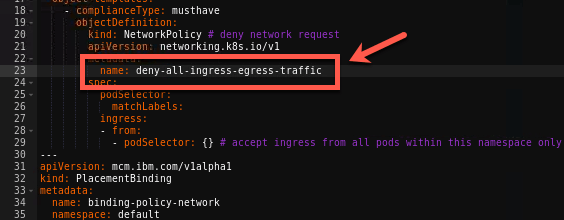
4.On the YAML file editor, change the objectDefinition > metadata > name from deny-from-other-namespaces to deny-all-ingress-egress-traffic.
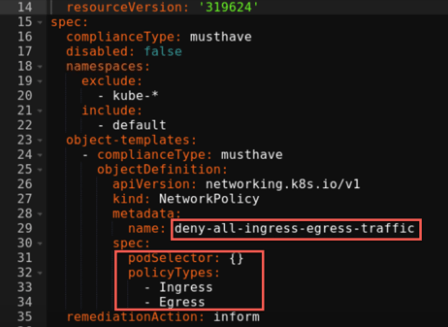
5.The spec section is defined as follow:
spec:podSelector: {}policyTypes:- Ingress- Egress
6.Keep remediationAction as inform by now. Click Create.
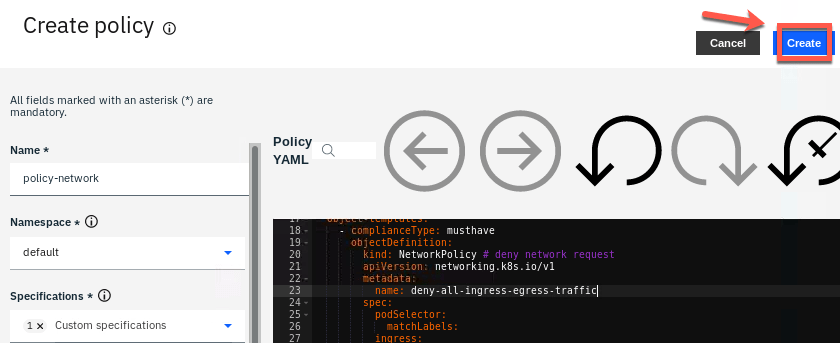
7.After few seconds, you should check that the policy violation was detected but not enforced.
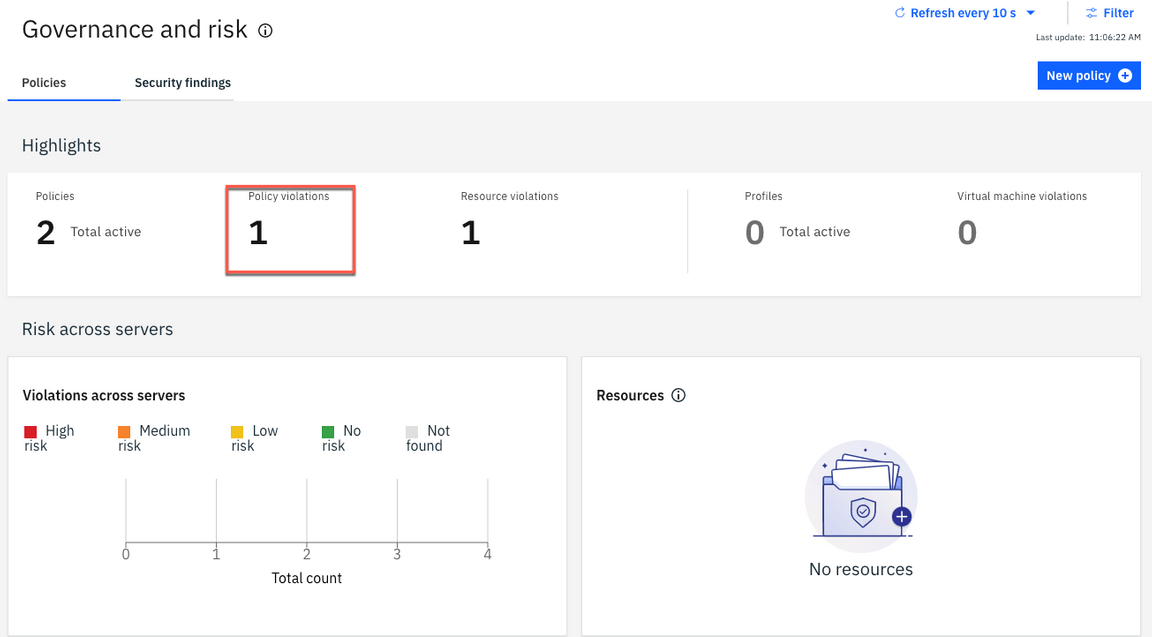
Because the policy is on inform mode, the policy is not forced.
8.Scroll down, and click on the new policy: policy-network.
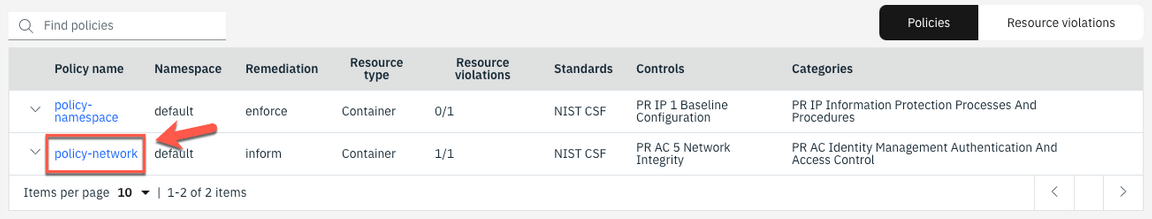
9.You see that one decision is in violation.
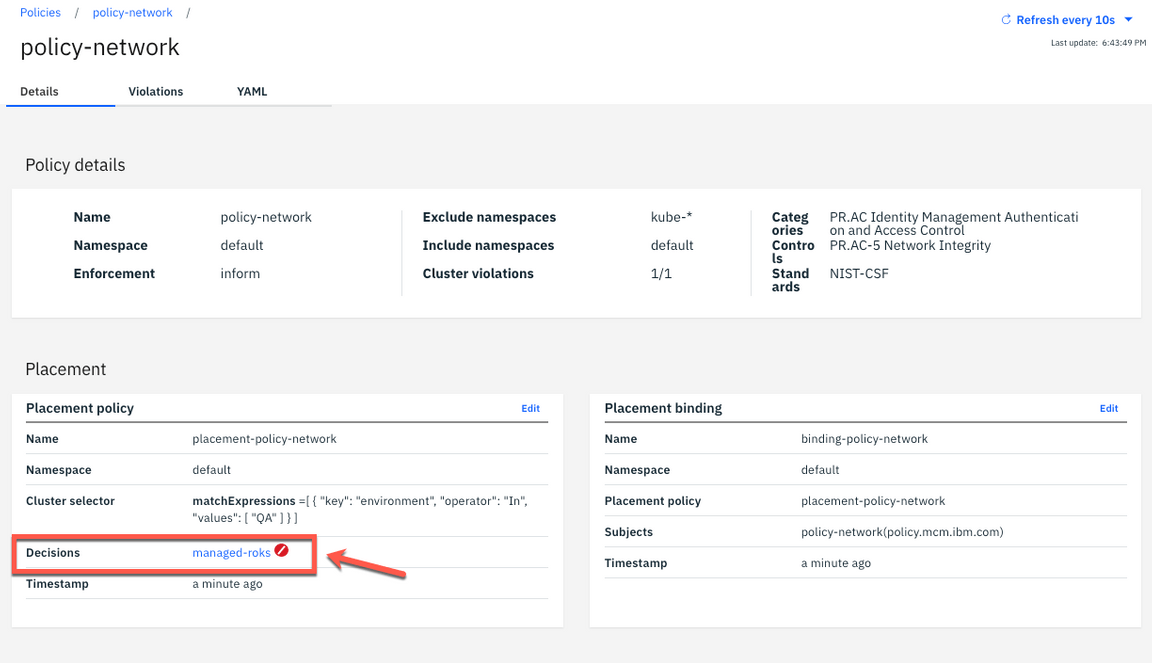
10.Click the Violations tab.
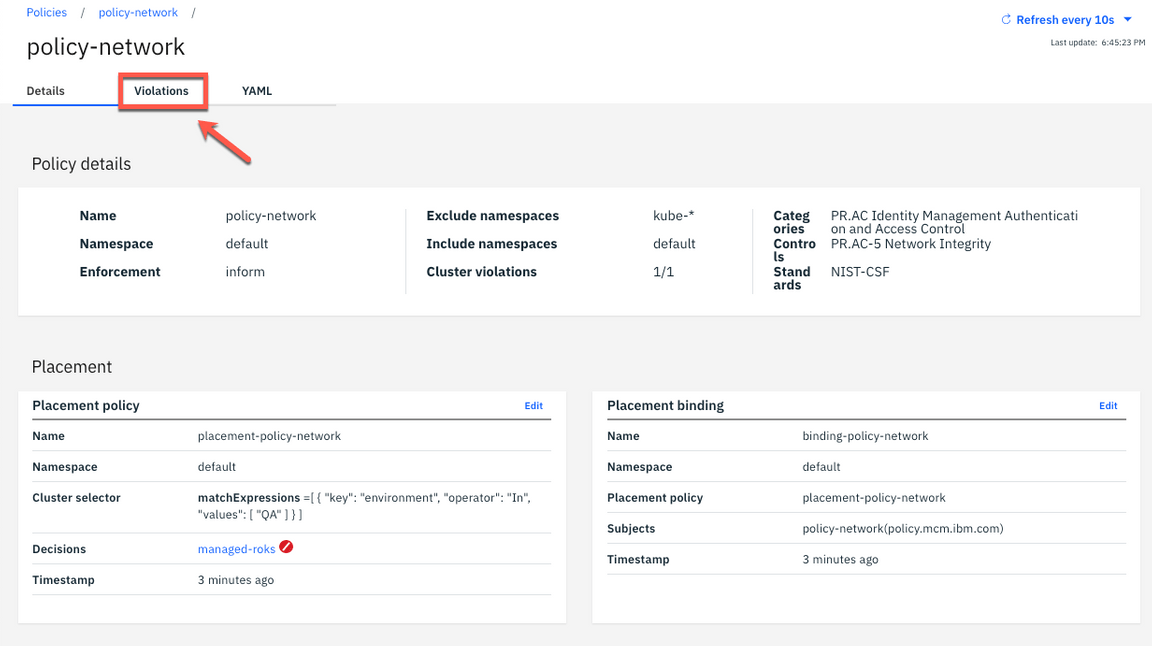
11.Here you see the violation about network isolation. Your local-cluster is not compliance with this network policy. Let’s fix it!
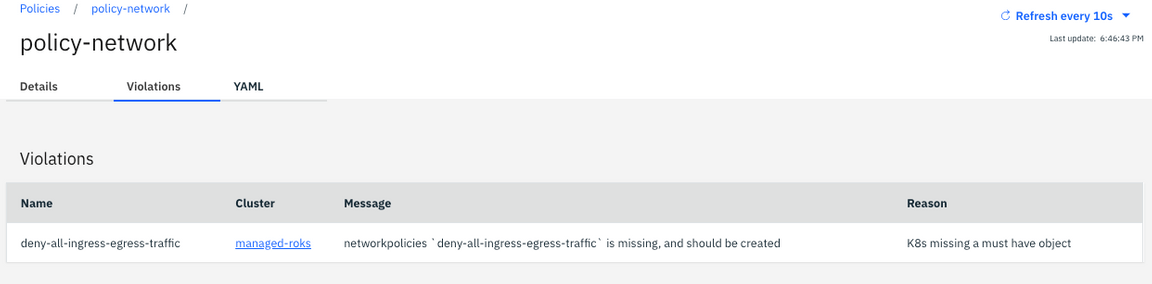
12.Click on managed-roks link to open the OpenShift Web Console of your Managed Cluster.
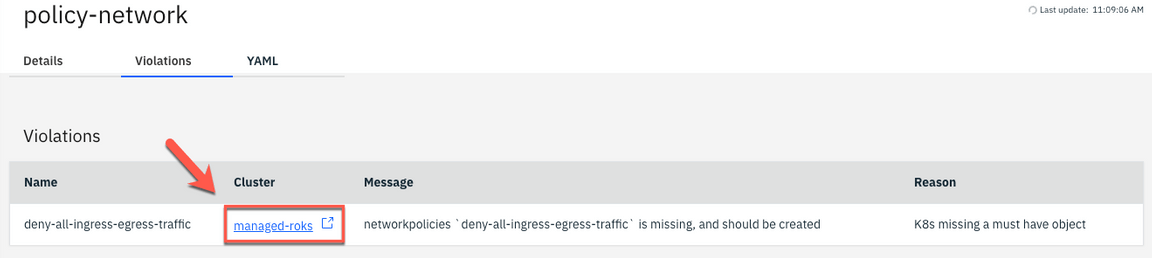
13.Use the side bar menu and select Networking > Network Policies.
14.Click the Create Network Policy button.

15.On the right, open the Samples tab.
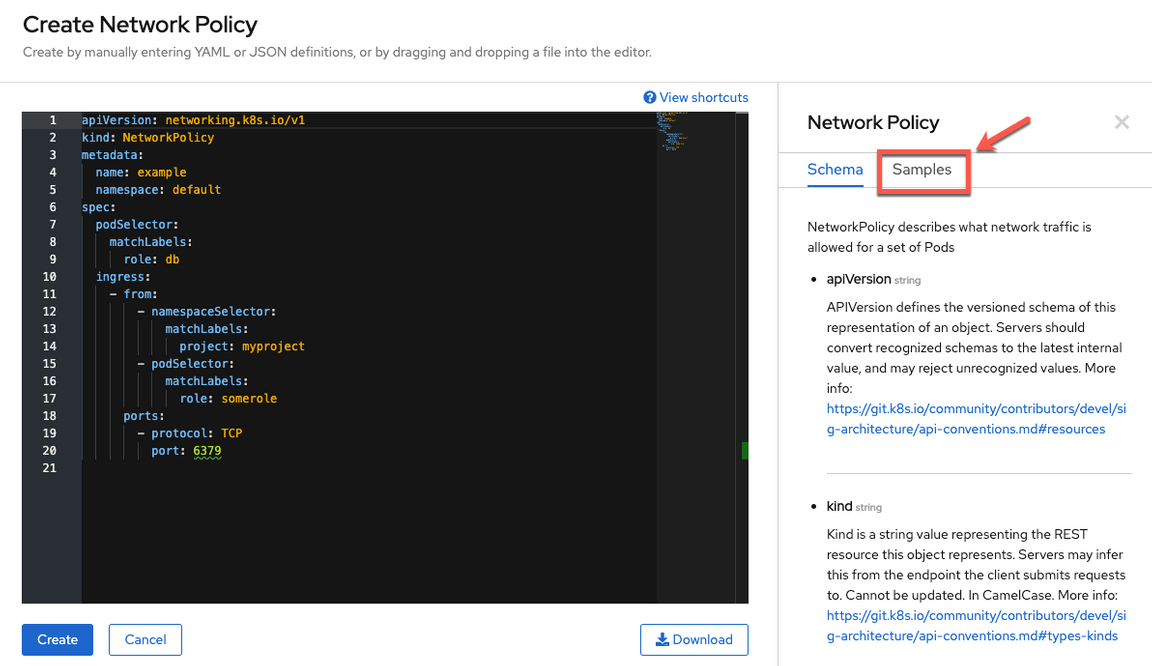
16.On the Samples tab, there are a list of policy samples. Fortunately for us, there is a Network Policy Sample that we can use. Click the Try it link (1). Then edit the YAML, by replacing deny-other-namespaces to deny-all-ingress-egress-traffic (2). Click the Create button to create this policy (3).
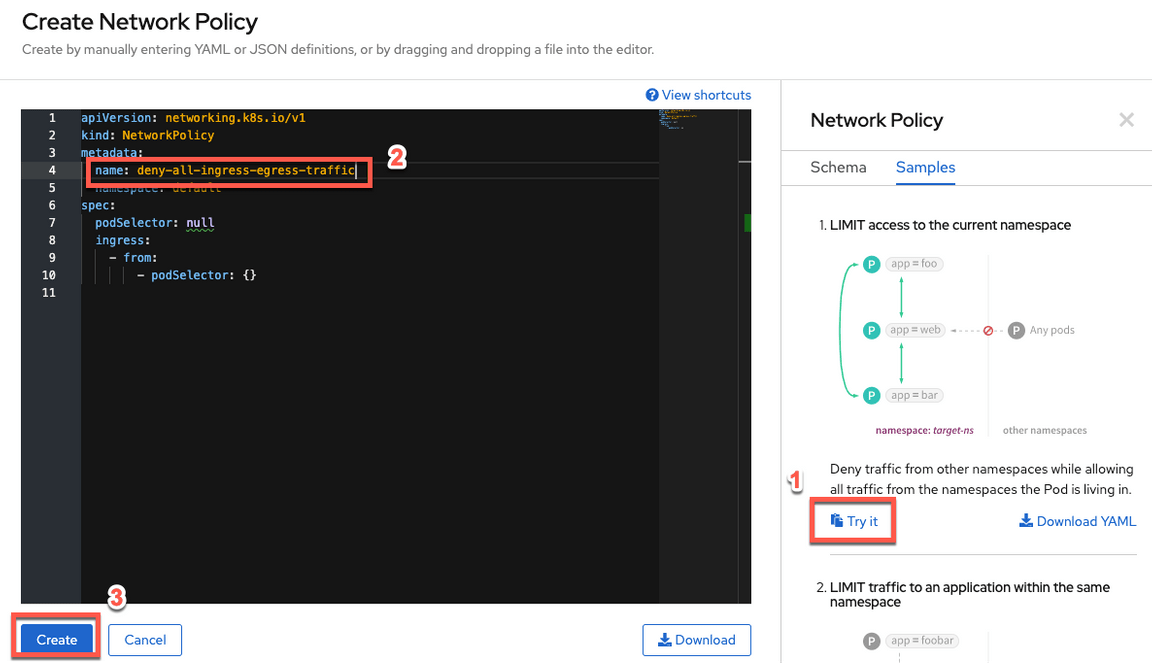
17.Great the policy is created now.
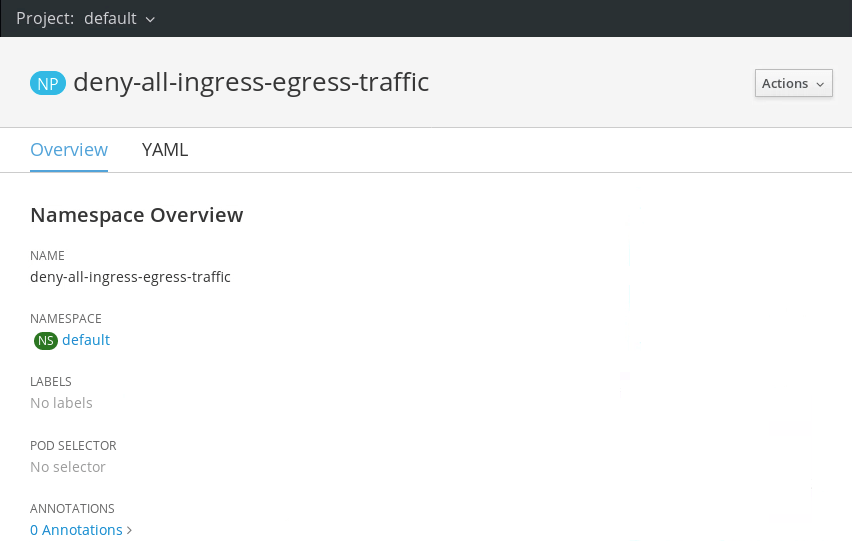
18.Go back to the CP4MCM browser tab. You should notice that there are no violations now (wait 10 seconds if you have to).
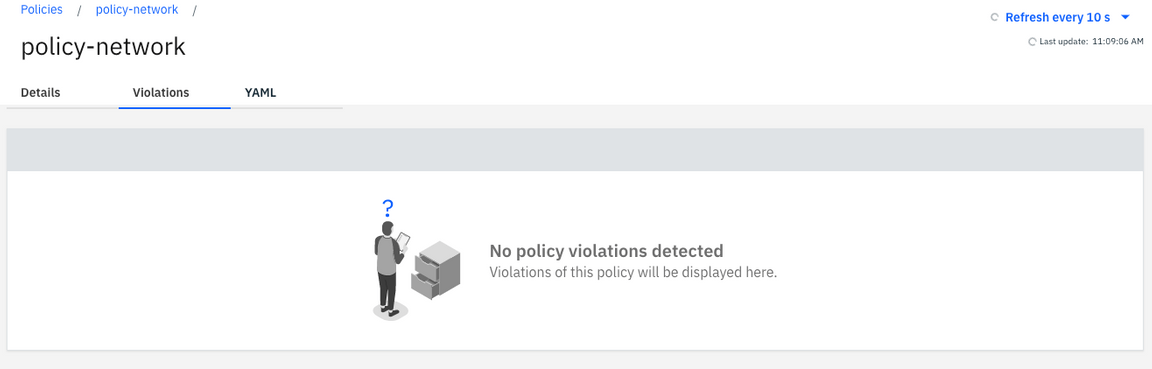
19.Click on Policies link in breadcrumbs, to go back to the Policies page.
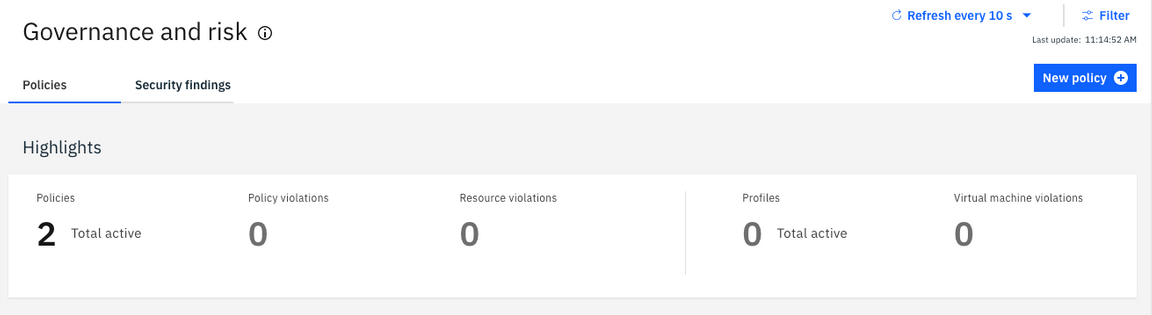
20.After waiting 10 seconds, you should see that all violations are gone.
Great! You have successfully implemented Network Policy!
Summary
You completed the Cloud Pak for Multicloud Management tutorial: Security & Compliance Management. IBM Cloud Pak for Multicloud Management governance, risk and compliance framework helps create custom policy controllers. You learned in the Lab how to create and customize policies with the out of the box policy templates.
If you would like to learn more about Cloud Pak for Multicloud Management, please refer to:
